Virtual Private Network (VPN)
A virtual private network
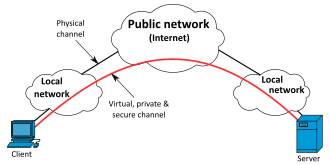
(VPN) protects your data and identity over public networks, like the Internet
and wireless hotspots. Various protocols are used to create an encrypted tunnel
that transports data securely. While a firewall may protect the data on your
computer, a VPN will protect your data on the Internet. The goal of a VPN is to
implement the same level of security provided by private networks at
substantially lower costs.
Why use a VPN?
Most VPN's are used to
add security. Today's world is evolving quickly and the security pitfalls of
modern conveniences are often ignored. Public WIFI hotspots, common in airports
and coffee shops, are a hackers dream because they offer streams of visible
data waiting to be mined. Using a VPN keeps your information secure.
Deep Packet inspection is
another growing concern. Many ISPs would like to analyze statistics from your
online activities for marketing and routing purposes. Using a VPN thwarts
efforts to conduct deep packet inspections.
Similarly, search engines
and social networking sites, like Google and Facebook, are storing information
about your online habits indefinitely. Since a VPN provides the user with a
different IP address, these privacy invasions are also thwarted.
VPN services provide
different gateway cities where the IP address assigned to your computer is
located. This allows users to access websites only available to users from a
certain country. This application is particularly important for travelers who
need to access websites from their home country and for people living in
regions rife with censorship, like China and Iran.
Protocols
PPTP is the most common
VPN protocol. It uses TCP port 1723 and Generic Routing Encapsulation (GRE) to
secure packets. The main advantage of PPTP is that all major operating systems
and many smart phones can natively use PPTP without any additional software.
IPsec is a protocol suite
developed with IPv6 and often used in conjunction with L2TP tunneling. IPSec
VPN services usually require third party software. Associated licensing costs
are one of the largest cons of IPsec.
SSL/TLS is the most common
encryption protocol on the Internet. Many SSL VPN plans use the OpenVPN client.
This free, multi-platform client and the vibrant community that supports it
have helped SSL VPNs rise to prominence.
SSTP is the newest
popular protocol. It transports PPP or L2TP packets through an SSL 3.0 channel.
Since SSTP uses the common HTTPS port 443, it is hard to block in highly
censored regions, like the Middle East. Unfortunately, SSTP is only available
on Windows Vista and Windows 7 computers.
Pay VPN Service Providers
CyberGhost VPN
Hide My Ass
TunnelBear
NordVPN

Comments
Post a Comment