Useful WMIC command in Windows
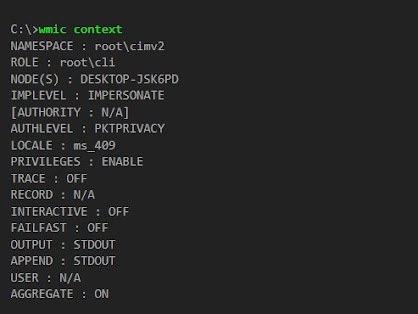
The WMI command-line (WMIC) utility is deprecated as of Windows 10, version 21H1, and as of the 21H1 semi-annual channel release of Windows Server . This utility is superseded by Windows PowerShell for WMI. Useful wmic command examples in Windows Example 1 : How to Display the State of all the Global Switches in Windows If you want to check the state of all global switches in windows then you need to use wmic context command as shown below. Example 2 : How to Get Your System Serial Number If you want to check your system serial number then you need to use wmic bios get serialnumber command as shown below. Example 3 : How to Check HotFixID of all the Installed Updates in Windows If you want to check the HotfixID of all the installed updates in windows then you need to use wmic qfe list command as shown below. **Note: Please note that it is possible that some of the updates will show in "View Installed Updates" section but...